Biometric Security Measures Include Which of the Following
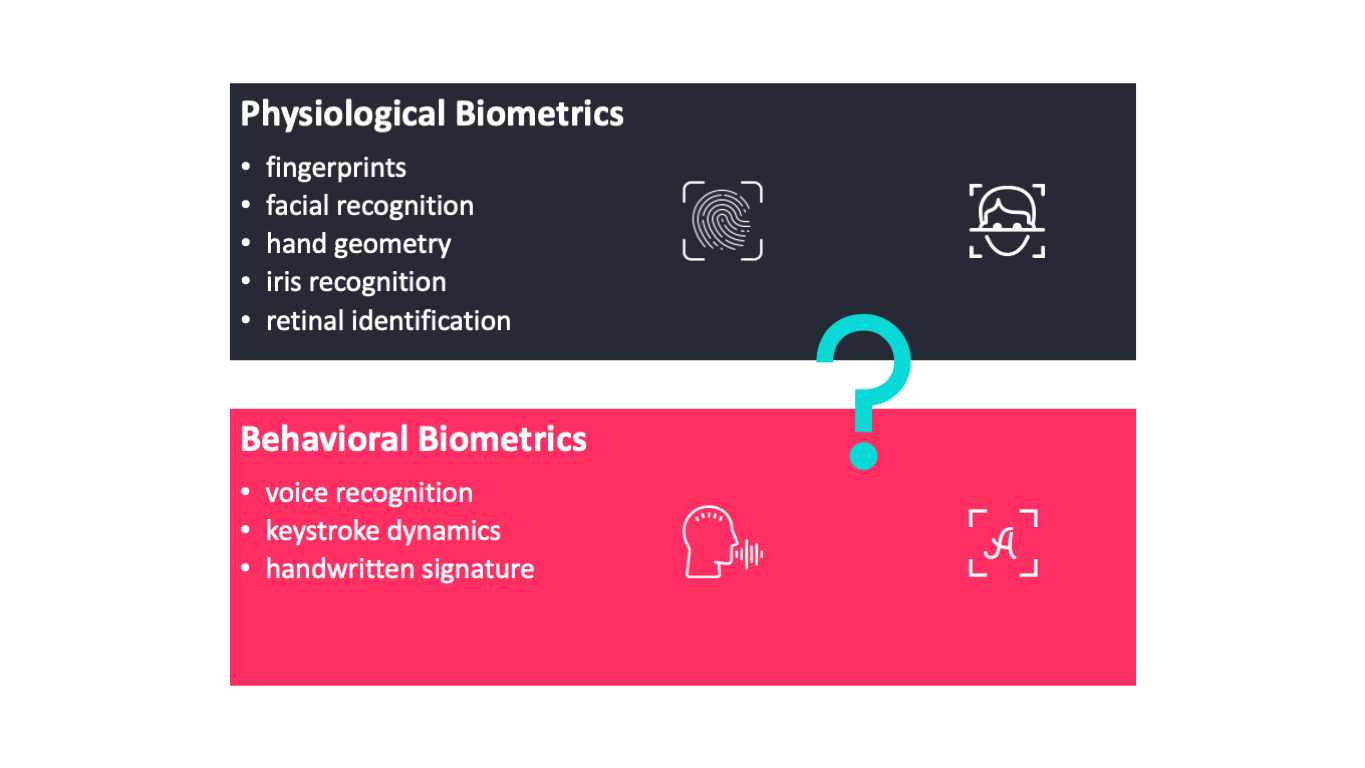
Physiological biometrics are those that rely on ones physical characteristics to determine identity. To be useful biometric data must be unique permanent and collectible.

Fingerprint Attendance System Measure Organic Components Like Human Highlights With A Spec Fingerprint Device Biometric Devices Fingerprint Attendance System
This category can include criminal ID.

. 1 Law enforcement and public security Law enforcement biometrics refers to applications of biometric systems that support law enforcement agencies. Traditional security and biometric security. The identification of the individual becomes easy and specified through the physiological biometrics.
Which of the following biometric security measures compares the length of each finger the translucence of fingertips and the webbing between fingers against stored data to verify users identities. Biometric authentication or realistic authentication is used in computer science as a form of identification and access control. _____ security measures primarily control access to computers and networks and they include devices for securing computers and peripherals from theft.
This security process is referred to as biometric authentication and is reliant on individuals unique biological characteristics to identify the individual correctly. Which of the following security measures is usually found in a laptop. Biometrics is presently a buzzword in the domain of information security as it provides high degree.
It is also used to identify individuals in groups that are under surveillance. Biometric Security Devices and Their Use. A firewall security measure.
They store search and retrieve fingerprint images and subject records. Biometrics are physical security mechanisms which deny any unauthorised access via authentication. Individuals produce a distinctive heartbeat regardless of their heart rate and level of exertion that is determined by a number of factors.
Different Types of Physiological Biometrics. Which of the following security measures is usually found in a laptop. Biometrics are body measurements and calculations related to human characteristics.
Biometric identifiers are the distinctive measurable characteristics used to label and describe. Physiological biometrics refers to the physiological features of a person by which he or she is recognized. Which of the following biometric security measures compares the length of each finger the translucence of fingertips and the webbing between fingers against stored data to verify users identities.
Biometric technologies being a newer technology have the potential to replace passwords and aid law enforcement in finding criminals. These features include facial features fingerprints iris and retina patterns. Which of the following security measures is a form of Biometrics.
This biometrics type includes but is not limited to the following. Biometrics is a branch of information technology that aims towards establishing ones identity based on personal traits. These can include physiological traits such as fingerprints and eyes or behavioral characteristics such as the unique way youd complete a security-authentication puzzle.
5 Biometric Security Measures to Keep You Safer in 2019 Voice face recognition gait analysis and palm are some of the biometric technologies that help id. 5 Biometric Security Measures to Keep You Safer in 2019. Hand geometry biometric systems incorporate the salient features of finger geometry but also include the surfaces of the hand itself and its side profile.
Solutions such as Automated Fingerprint and palm print Identification Systems AFIS. The term Biometrics is composed of two words Bio Greek word for Life and Metrics Measurements. This article takes a comparative approach to discuss traditional and biometric approaches of security and tries to draw a.
Which of the following did the technician forget to do to prevent reinfection. The different types of biometric security devices entail using biometric security software to verify individuals by considering their biological or behavioral features. Connect to the network and update the OS with the latest security patches B.
Fingerprint recognition which measures a fingers unique ridges is one of the oldest forms of biometric identification. One of the most wellknown examples of a biometric recognition system is the iPhones fingerprint and face recognition technology. Facial recognition gait analysis and behavioral palm and voice biometrics are some of todays cutting-edge biometric technologies that.
Once measured the information is compared and matched in a database. The security measures we take can be largely divided into two major categories. Key fobs Show Answer.
These traits can be used instead of passwords to verify and identify individuals as they are bound to the individual. Scan and clean the USB device used to transfer data from the equipment CompTIA 220-1002 Exam Pass Any Exam. Owing to its low cost fingerprint recognition is the most common technology used in these devices.
Simply put biometrics are any measures relating to human characteristics. The security of the biometric authentication data is vitally important even more than the security of passwords since passwords can. Because biometric security evaluates an individuals bodily elements or biological data it is the strongest and most foolproof physical.
Seenagape June 26 2013.

Know How You Can Save Your Mission Critical Business Data With Data Center Services Business Data Data Security Data Loss

Measuring Your Biometrics 18 X 24 Poster Health Poster Biometrics Health Screening Health

Biometric Technologies Market Share Biometrics Technology Biometrics Voice Biometrics
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

Scp Foundation Secure Access Id Card Our Original Version Etsy In 2022 Scp Foundation Scp Containment Breach

Biometric Security Biometric Security Biometrics Technology

Bio Face Reader Biometrics Face Recognition Face

Biometrics In The News Mastercard Plans For Transaction Implementation In 2019 Ark Systems Inc Biometrics Multi Factor Authentication Identity Theft

Security Measures To Be Taken While Developing A Mobile Application Mobileapps Mobile Application Mobile App Development Companies Mobile App Development

What Is Biometric Payment And How Does It Work

Pin On Technology Infographics

Advanced Biometric Technology To Be Deployed Globally Ihls Biometrics Biometric Authentication Learning Technology

Biometric Mastercard With Fingerprintreader For More Security Measures Https Www Tigmoo Com Blog Biometric Card W Biometrics Fingerprint Reader Mastercard

San Diego Biometric Digital Security It Services Computer Security San Diego Biometrics Biometric Security Computer Security

Biometric Access Control Systems Security Measures And Principles

How To Set Up Lock Screens On All Your Devices In 2022 Lockscreen Feeling Frustrated Security Screen

Engineers Develop A Car That Can Monitor Your Health As You Drive And Take Over If You Become Ill Or Fall Asleep Biometrics Ford How To Fall Asleep

Biometric Attendance Systems Biometrics Biometric System Access Control

Biometrics Grow In Both Popularity And Application Fiberplus Inc Access Control System Biometrics Access Control
Comments
Post a Comment